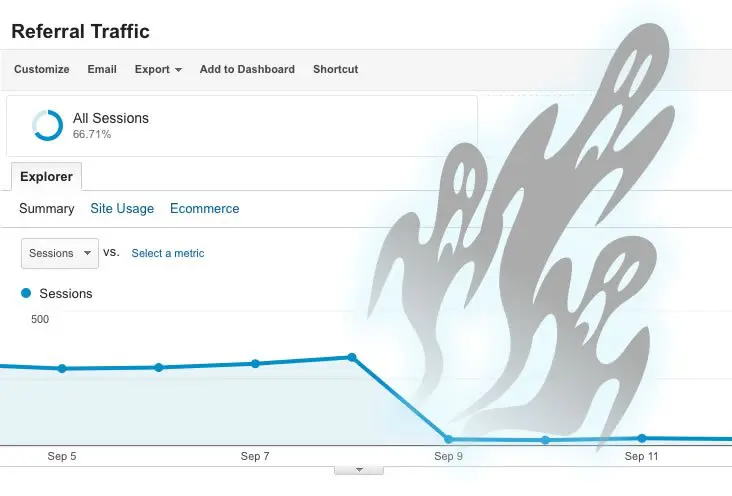
What is ghost spam? “Ghost spam” is a term that means that someone is posting spam on other websites without actually registering as a user. The spammer will use open proxies to log in and post false information, making it hard for the site. Or its administrator to know who they are or where they are posting from. Anyone who cannot get enough accounts on their own can use ghost spamming. This happens because of spam prevention measures like captchas. Find out what ghost spam is and more about it by reading this full article.
Ghost spamming is an indirect use of botnets to send spam. Using a botnet can get more than one IP address that the spammer can use at once. The botnet will then forward the connection to other users’ computers that share the same IP address as the original malicious user.
Types of Spam
Here are a few types of spam you may encounter. Let’s find out more about them:
- Ghosts
Malicious users who try to create fake accounts on users’ websites. Ghosts usually “like” friends’ statuses, leave comments, and send friend requests. They may also have a different IP each time they visit the victim’s page. Ghosts can be either local or remote. A local ghost is someone who has accessed the IP address that belongs to the victim. Usually through malware from an external source.
- Crawlers
Multiple fake accounts on other users’ websites that can be controlled from the same IP. The spammer will then forward the connection to other users’ computers with the same IP address as the original malicious user.
Most common mistakes made when dealing with spam in GA
Google Analytics is crucial when it comes to website health and traffic. It conducts no effort to identify whether or not the account registered with Google Analytics belongs to your company or an outside source. This is because they have their own set of priorities.
- Blocking ghost spam from the .htaccess file
If you’ve been using htaccess to block spam from comments and trackbacks, ghost spam will go directly through since it isn’t included in the configuration.
- Using IP blocks
Since ghost spam comes from a different IP each time, it is necessary to use a script to block them. If your site uses a shared IP address or has multiple users linking to one site, then you need to use a script that will identify the malicious user.
- Using the referral exclusion list to stop spam
If you’re using this report to get rid of ghost spam, it’s a good idea to check that the IP is not one of the referrers on the exclusion list. Since the ghost spam comes from different IP addresses each time.
- Breaking out of a loop
The best way to avoid this problem is by ensuring that each time your site checks for spam and ghosts. It has to do so using a different IP address.
- Bounce rate will affect rankings
Ghost spam will still cause a drop in the bounce rate, but it shouldn’t affect the pages’ rankings.
- Tracking down who is ghost spamming
Block ghosts by using this script. If you’re using a shared IP address, you will need to use the referral exclusion list or add a script that will identify the malicious user to block them from linking to your site. This script may also help track down where users are coming from since they share an IP address.
- Assuming your site has been hacked
It is hard to know if your entire site has been hacked or if only one page has been hacked. Since the hacker will use a script to redirect the malware onto other websites without you knowing. To eliminate ghost spam, you must use protocols and scripts that identify these ghosts before they can disrupt your website.
- You only need one filter to deal with ghost spam
If you need to set up a filter that will check all of the entries in your database at once, then you should use this script. You can edit it so that it will check all of the entries in Google Analytics. And will send you an email when a ghost spammer has been identified.
- Bonus resources to help you manage spam
Captchas are an excellent way to prevent ghost spam. While most services will use them for security, some may use them for other purposes, such as to get more revenue from advertisements and by allowing people to post comments or friend requests. Any database with IP addresses should include a list of names and IP addresses. This ensures that you have a means of finding out who is posting on your site without having to do any of the work yourself.
Final Words
So are you clear about ghost spam now? It is possible for large websites with a lot of traffic to also be affected by spam. And while it may be insignificant, false traffic leads to inaccurate reports regardless of the size of the site. You should be able to explain even the most granular reports as an SEO analyst. Hopefully our round will be helpful for you in this regard.



















Leave a Reply
View Comments